Credential Theft Costs $4.8M Per Breach: The Case for Zero-Knowledge Authentication
January 20, 2026 by Nick Morgan

Stolen credentials represent the #1 attack vector in data breaches, responsible for 38-49% of all security incidents and costing organizations an average of $4.81 million per breach.
Traditional password-based authentication cannot be fixed through policy or training because it contains inherent vulnerabilities. Eliminating usernames and passwords entirely through zero-knowledge architecture addresses this attack vector at its source.
Credential Theft: The Dominant Attack Vector
Every major cybersecurity report confirms what security professionals have long suspected: stolen credentials have become the primary method for breaching enterprise systems. Unlike sophisticated zero-day exploits or advanced persistent threats, credential-based attacks succeed through a simple mechanism. Attackers use valid usernames and passwords to walk through the front door. This attack vector outpaces phishing, malware, and vulnerability exploitation combined, representing the single greatest authentication failure facing modern enterprises.
Fact 1: Stolen or compromised credentials rank as the most common initial attack vector, accounting for 16% of breaches in IBM’s analysis, higher than any other single cause.
Fact 2: Verizon’s Data Breach Investigations Report found that 38% of breaches analyzed used compromised credentials, more than double the share involving phishing or vulnerability exploits.
Fact 3: Historical analysis shows approximately 49% of all breaches involve stolen credentials in some manner, making it the dominant breach method over the past decade.
Fact 4: Credential-based attacks increased 71% year-over-year, representing the fastest-growing threat vector in enterprise security.
Fact 5: Between 86-88% of breaches in the “Basic Web Application Attacks” category involve the use of stolen credentials. Attackers aren’t exploiting zero-day vulnerabilities, they’re using valid logins.
Zero-knowledge authentication architectures eliminate this attack vector by removing credentials from the authentication process entirely. When no usernames or passwords exist to steal, credential theft becomes impossible.
Learn more about zero-knowledge authentication architecture
The Dark Web Credential Economy
The underground market for stolen credentials operates at industrial scale, fueling the credential theft crisis. Criminal marketplaces function as efficient distribution channels where compromised authentication data moves from breach point to attacker within hours, creating a self-sustaining ecosystem that makes password-based security increasingly untenable.
Fact 6: Over 1,000 stolen credentials are posted for sale on dark web marketplaces daily, providing continuous supply of fresh authentication data to attackers.
Fact 7: The average price for stolen credentials is just $10 per account, making credential-based attacks extraordinarily cost-effective for attackers compared to developing custom exploits.
Fact 8: 65% of stolen credentials appear on dark web marketplaces within 24 hours of being compromised, giving attackers near-real-time access to valid authentication data.
Fact 9: Verizon characterizes stolen credentials as “keys to the kingdom” for threat actors, providing direct access to VPNs, cloud environments, and critical business applications without triggering security alerts.
This underground economy thrives because password-based authentication creates persistent, stealable assets. Distributed authentication architectures that bind identity to physical devices render this market irrelevant. Even if attackers obtain session data, authentication requires possession of the registered device, making stolen data fragments mathematically useless.
Explore distributed data architecture
Financial Impact: The Multi-Million Dollar Breach Cost
The financial consequences of credential-based breaches extend far beyond immediate incident response costs. Organizations face a cascade of expenses including forensic investigation, legal fees, regulatory penalties, customer notification, credit monitoring services, system remediation, and long-term reputation damage. These costs have been rising steadily year-over-year, with no indication of the trend reversing under traditional authentication models.
Fact 10: The global average cost of a data breach reached $4.88 million, representing a 10% year-over-year increase.
Fact 11: Breach costs have increased 15% over three years, with credential-based attacks driving a significant portion of this growth.
Fact 12: Breaches specifically initiated through compromised credentials average $4.81 million per incident, essentially matching the overall breach average and demonstrating that stolen passwords are just as financially devastating as more sophisticated attack methods.
Fact 13: Global cybercrime damages, which include data breach losses, are projected to reach $10.5 trillion annually.
Fact 14: Over 3,200 publicly reported data compromises impacted an estimated 353 million individuals, a 78% increase in affected people from the previous year.
Fact 15: Breaches identified and contained in under 200 days cost approximately $1.02 million less than those taking longer, representing a 23% cost reduction for faster detection and response.
Preventing credential-based breaches, which account for 38-49% of all incidents, delivers immediate ROI. The average $4.81 million credential breach cost far exceeds the implementation expense for passwordless authentication across even large enterprise environments. Additionally, authentication methods that trigger immediate alerts for unauthorized access attempts enable dramatically faster breach detection compared to the 292-day average for credential attacks.
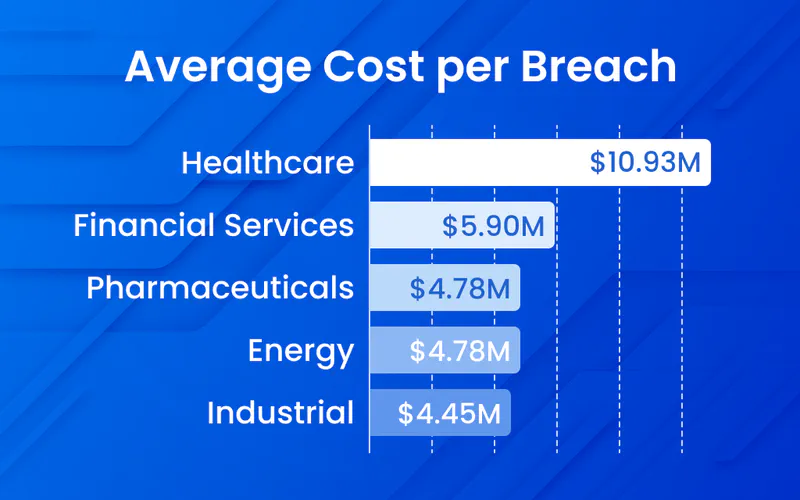
Industry-Specific Breach Costs: Healthcare and Financial Services
While all sectors face credential theft risks, certain industries experience disproportionate financial and operational impact. Healthcare and financial services consistently rank as the costliest sectors for data breaches, driven by regulatory compliance requirements, high-value data targets, and extensive customer notification obligations. These industries represent priority deployment targets for passwordless authentication technologies.
Fact 16: Healthcare organizations experience the highest average breach cost of any industry at $10.93 million per incident, nearly 2.5 times the global average.
Fact 17: Healthcare breach costs have increased 53% over three years, reflecting both rising attack frequency and expanding regulatory penalties.
Fact 18: 809 healthcare data breaches were reported, representing the highest volume of any industry sector.
Fact 19: Healthcare breaches take an average of 213 days to detect compared to 194 days in other sectors, extending exposure time for protected health information. (Source: IBM
Fact 20: Financial services organizations face the second-highest breach costs at $5.90 million average per incident.
Fact 21: The financial sector experienced 3,300+ security incidents and 1,100+ confirmed data breaches, representing one of the highest incident counts among all industries.
Fact 22: Financial sector breaches increased from 19% to 27% of total breach activity year-over-year, indicating accelerating targeting of financial institutions.
Fact 23: 22% of finance sector breaches started with stolen credentials, the single largest attack vector in financial services.
Fact 24: Financial services experienced an 80%+ increase in interactive intrusion attempts, many involving credential misuse for lateral movement within networks.
Zero-knowledge authentication provides particular value in heavily regulated sectors. For healthcare, eliminating password storage and transmission during authentication addresses HIPAA compliance requirements. The absence of centralized credential databases removes primary breach targets. In financial services, passwordless authentication integrates with Microsoft Entra ID, Azure, and M365 environments common in banking infrastructure while meeting phishing-resistant authentication requirements from financial regulators.
Large Enterprise and Critical Infrastructure Costs
Organizations with extensive IT footprints and thousands of employees face exponentially higher breach costs than small businesses. The combination of larger attack surfaces, more valuable data repositories, complex multi-environment architectures, and extensive third-party integrations creates compound risk. Critical infrastructure sectors including energy, technology, and industrial manufacturing face additional consequences beyond direct financial loss, including potential cascading failures affecting essential services.
Fact 25: Large enterprises with 75,000+ employees average $25.6 million to resolve credential-related insider incidents, compared to approximately $8 million for organizations with fewer than 500 employees.
Fact 26: Breaches affecting data across multiple environments including cloud and on-premises systems cost over $5 million on average and take 283 days to identify and contain.
Fact 27: Critical infrastructure organizations including healthcare, financial, industrial, technology, and energy sectors incur the highest breach costs among all industries.
Fact 28: The United States experiences the highest country-level average breach cost at $9.48 million per incident.
Fact 29: 63% of breached organizations pass costs to customers through price increases, creating competitive disadvantage and customer trust erosion. (
Username-less and passwordless authentication scales without increasing operational complexity. Unlike password management systems that require more helpdesk resources, reset infrastructure, and policy enforcement as user populations grow, authentication without credentials maintains consistent operational overhead regardless of organization size. A single platform can span on-premises legacy systems, private cloud environments, public cloud services, and SaaS applications through standard protocol support.
Explore enterprise authentication integration
The Detection Time Crisis
One of the most damaging aspects of credential-based breaches is the extraordinary time required for detection and containment. Unlike malware infections or network intrusions that may trigger automated alerts, attackers using stolen credentials appear identical to legitimate users in authentication logs. This “silent breach” phenomenon allows attackers to maintain persistent access for months, exfiltrating data, escalating privileges, and establishing backdoors while security teams remain unaware of the compromise.
Fact 30: Breaches involving stolen or compromised credentials take an average of 292 days to identify and contain, the longest detection time of any attack vector.
Fact 31: The global average breach lifecycle improved to 258 days but still represents over 8 months from initial intrusion to full containment.
Fact 32: Only 33% of credential breaches are detected by the victim organization’s own security team. The majority are discovered by external parties, law enforcement, or become apparent when attackers deploy ransomware.
Fact 33: Only 42% of all breaches were detected internally by organizations’ own security tools, though this represented improvement from 33% the previous year.
Fact 34: Attackers using stolen credentials appear identical to legitimate users in authentication logs, making security monitoring unable to distinguish compromised accounts from normal user activity.
The extended dwell time for credential breaches directly correlates with higher financial costs and greater operational damage. During the 292-day average breach lifecycle, attackers can exfiltrate entire databases, compromise backup systems, and establish persistent access mechanisms that survive initial remediation efforts. Device-bound authentication eliminates this detection problem by changing the authentication model fundamentally. Authentication attempts without the registered physical device fail immediately and generate security alerts. There is no multi-month period of silent compromise because the architecture prevents unauthorized access at the first attempt rather than relying on behavioral analytics to detect anomalies months later.
Operational Burden: The Hidden Cost of Password Management
Beyond breach costs, password-based authentication imposes significant operational burden on every organization. IT helpdesks spend substantial resources on password resets, account unlocks, and user support. Employees lose productivity to forgotten passwords and locked accounts. Security teams manage password policy enforcement, complexity requirements, rotation schedules, and breach response. These operational costs persist regardless of whether breaches occur, representing permanent friction in business operations.
Fact 35: Between 20-50% of all IT helpdesk calls involve password resets, consuming substantial support resources on non-value-adding activities.
Fact 36: Each password reset costs an average of $70 in support labor when accounting for helpdesk time, user productivity loss, and system overhead.
Fact 37: Large enterprises spend over $1 million annually on password-related support costs alone, not including breach-related expenses.
Fact 38: Employees waste an average of 11 hours per year dealing with password issues, locked accounts, and reset procedures.
Fact 39: 70% of breached organizations reported significant or very significant business disruption from the incident, extending beyond direct financial costs.
Fact 40: Only 12% of breached organizations achieved full operational recovery within 100 days. The majority require months to restore normal operations.
Fact 41: Credential theft incidents average $680,000 in mitigation costs even before any actual breach occurs, representing the expense of responding to credential stuffing attacks, investigating compromised accounts, and implementing additional controls.
These operational costs provide additional ROI justification beyond breach prevention. For a 5,000-employee organization, the annual productivity loss alone totals approximately $2.75 million (55,000 employee hours at $50/hour average). Combined with $1 million in helpdesk costs and $680,000 in credential attack mitigation, the operational burden reaches $4.4 million annually, nearly matching the average breach cost. Eliminating credentials removes this entire cost category because passwordless authentication has no reset procedures, no lockout mechanisms, no policy enforcement overhead, and no credential stuffing attacks to mitigate.
The Unfixable Human Element
Security awareness training, password complexity policies, and multi-factor authentication represent attempts to strengthen password-based security. However, these measures cannot overcome fundamental human behavior patterns. Users will always choose convenience over security when forced to manage dozens of complex passwords. Even users who fully understand the risks continue unsafe practices because the authentication system demands behaviors incompatible with normal cognitive limitations and workflow requirements.
Fact 42: 61% of users reuse passwords across multiple accounts, both personal and professional, creating credential stuffing vulnerability.
Fact 43: 91% of users know that password reuse is unsafe, yet continue the practice anyway, demonstrating that awareness doesn’t change behavior.
Fact 44: 74% of breaches involve the human element, including errors, misuse of credentials, and social engineering attacks.
Fact 45: Traditional multi-factor authentication remains vulnerable to sophisticated phishing attacks using real-time proxy methods that capture both passwords and MFA codes.
Fact 46: Push notification fatigue enables MFA bypass. Users approve authentication requests without verification when overwhelmed by legitimate push notifications.
Fact 47: SIM-swapping attacks compromise SMS-based MFA by allowing attackers to intercept text message codes sent to mobile devices.
Fact 48: Many MFA implementations include backup authentication methods like security questions or email recovery that reintroduce credential exposure vulnerabilities.
Removing credentials from authentication eliminates the decisions users make incorrectly. There are no passwords to reuse, write down, share with colleagues, or enter into phishing sites. Authentication happens through device possession and biometric verification on smartphones or physical token possession with hardware keys, neither of which requires users to remember, create, or manage secrets. Dynamic authentication mechanisms are inherently phishing-resistant because there’s no credential to phish. Even if users interact with malicious authentication requests, attackers receive useless session data that cannot be replayed. This architectural approach sidesteps the human element rather than attempting to fix it through training or policy.
Understanding phishing-resistant authentication
Credential Stuffing and Automated Attacks
Beyond targeted breaches, organizations with password-based authentication face continuous automated attacks at massive scale. Botnets test billions of stolen username and password combinations against enterprise systems, attempting to exploit credential reuse. These credential stuffing campaigns create operational overhead, consume infrastructure resources, trigger account lockouts, and occasionally succeed when employees have reused passwords from previously breached services.
Fact 49: Credential stuffing attacks operate at tens of billions of login attempts globally, representing industrial-scale automated attacks against password-based systems.
Fact 50: Botnets continuously test username and password pairs obtained from previous breaches against enterprise systems, exploiting password reuse across services.
Fact 51: Organizations face continuous “siege” from automated credential attacks due to the sheer volume of stolen credentials circulating on dark web marketplaces and the minimal cost ($10 average) to acquire them.
Fact 52: Stolen credentials frequently serve as precursors to ransomware attacks. Attackers use valid logins for initial access, then move laterally through networks to deploy encryption malware.
Credential stuffing attacks become completely ineffective against systems without username and password authentication because there are no credential pairs to test. Authentication models that verify cryptographic proof tied to physical devices rather than checking credentials against databases cannot be attacked through automated testing.
Attackers cannot generate valid authentication attempts through automated scripts because they lack both the device and the distributed cryptographic keys required for verification. This eliminates not only the breach risk but also the operational overhead of defending against billions of automated login attempts.
Zero-Knowledge Architecture: Technical Foundation

Traditional authentication systems create inherent vulnerability by storing passwords or password hashes in centralized databases. Even when properly hashed and salted, these databases represent attractive targets for attackers. A single database breach potentially compromises thousands or millions of accounts. Multi-factor authentication adds layers but doesn’t eliminate the underlying credential storage vulnerability.
Zero-knowledge authentication eliminates this architectural weakness through distributed data models. Instead of storing credentials in centralized databases, authentication elements are mathematically split across multiple geographically distributed data centers. No single data center contains enough information to authenticate a user or reconstruct identity data. This provides mathematical certainty against centralized database breaches.
Modern passwordless authentication works through cryptographic challenge-response mechanisms:
No Static Credentials: Users don’t create, remember, or enter passwords. Authentication relies on cryptographic keys stored securely on registered devices including smartphones or hardware tokens. The device itself becomes the authentication token through public-key cryptography.
Dynamic Challenge-Response: Each authentication attempt generates a unique, time-limited challenge. The user’s device performs cryptographic operations using stored private keys and transmits the response. Even if an attacker intercepts this exchange, the data cannot be reused because the challenge changes with every authentication attempt.
Device-Bound Identity: Authentication absolutely requires physical possession of the user’s registered device. This creates inherent resistance to phishing because users have no credentials to give away, resistance to man-in-the-middle attacks because intercepted data cannot be replayed, and resistance to credential theft because no credentials exist to steal. Lost or stolen devices can be remotely deactivated, immediately revoking access without password reset processes.
Zero-Knowledge Verification: Authentication servers verify user identity without ever processing, storing, or having access to authentication secrets in readable form. The distributed architecture means the authentication service itself operates on zero-knowledge principles. It can confirm identity without knowing the underlying cryptographic keys. This makes passwordless systems inherently compliant with privacy regulations like GDPR and data protection standards like HIPAA.
Enterprise Protocol Integration: Modern passwordless platforms integrate with existing enterprise authentication infrastructure through standard protocols including SAML, OAuth2, RADIUS, LDAP, and Kerberos. This enables passwordless authentication for Microsoft environments including Entra ID, Azure, M365, and SharePoint, VPN access, wireless networks, legacy applications, and modern SaaS platforms. Organizations can implement passwordless authentication without replacing identity management systems because it layers on top of existing infrastructure.
ROI Analysis: The Business Case for Eliminating Passwords
The financial case for passwordless authentication implementation becomes clear when comparing prevention costs against breach statistics and operational expenses. Organizations should evaluate passwordless authentication not as a security enhancement but as risk elimination for the #1 attack vector responsible for 38-49% of breaches.
Breach Cost Avoidance: For an organization facing a $5 million average breach cost, typical for mid-size enterprises in regulated industries, the credential attack risk exposure equals $5M × 0.38 = $1.9 million. Eliminating this attack vector provides $1.9 million in annual risk reduction. Even preventing a single credential breach over a five-year period delivers 10:1 or greater ROI compared to passwordless authentication deployment costs.
Operational Cost Elimination: A 5,000-employee enterprise experiences approximately $4.4 million in annual password-related operational costs: $2.75 million in employee productivity loss (11 hours × 5,000 employees × $50/hour), $1 million in helpdesk support costs, and $680,000 in credential attack mitigation. Passwordless authentication eliminates these expenses entirely because there are no reset procedures, no helpdesk calls, no productivity loss from forgotten passwords, and no credential stuffing attacks to defend against.
Detection Time Advantage: Organizations that detect and contain breaches in under 200 days save approximately $1.02 million compared to slower response, a 23% cost reduction. Device-bound authentication enables immediate detection of unauthorized access attempts because authentication without the physical device fails immediately and triggers alerts. This places organizations in the fast-detection category even for non-credential attack vectors by improving overall security monitoring and response capabilities.
Combined Annual Value: For a 5,000-employee enterprise: $1.9M breach risk reduction + $4.4M operational cost elimination + $1M detection time advantage = $7.3 million total annual value. This doesn’t include additional benefits like cybersecurity insurance premium reductions, regulatory compliance improvements, competitive advantage from superior security posture, or customer trust enhancement.
The ROI calculation becomes even more compelling for high-risk sectors. Healthcare organizations averaging $10.93 million per breach and financial services at $5.90 million face proportionally higher risk exposure that eliminating credentials addresses. Large enterprises with 75,000+ employees spending $25.6 million on credential-related incidents see correspondingly larger operational cost savings.
Implementation Path for Microsoft-Centric Environments
Most enterprises operate Microsoft-centric IT environments with Active Directory, Entra ID (formerly Azure AD), Microsoft 365, SharePoint, and Azure cloud services. Passwordless authentication integrates natively with this ecosystem, enabling credential elimination without disrupting existing identity management infrastructure or requiring wholesale platform replacement.
Microsoft Entra ID Integration: Passwordless platforms connect directly to Microsoft Entra ID through SAML federation, providing authentication without credentials for all Entra-connected applications. Users access Microsoft 365, Azure Portal, SharePoint, Teams, and third-party SaaS applications without entering passwords. This creates a single sign-on experience across the Microsoft ecosystem without credential exposure.
Gradual Migration Strategy: Organizations can implement passwordless authentication through phased rollout beginning with highest-risk populations. Initial deployment targets privileged accounts including administrators and executives, plus high-value systems like financial applications and customer data repositories. This immediately protects the most likely breach targets while allowing time for broader deployment planning. Users can be provisioned with passwordless authentication while legacy password methods remain available for non-critical systems during the transition period.
Protocol Support Across IT Landscape: Modern passwordless platforms support the full range of enterprise authentication protocols, enabling credential elimination across diverse systems:
- RADIUS for VPN authentication, wireless network access, and network device management
- LDAP for directory services integration and legacy application authentication
- Kerberos for Windows domain authentication and file server access
- SAML/OAuth2 for modern web applications, SaaS platforms, and cloud services
- Authentication proxies for legacy systems without native modern protocol support
This comprehensive protocol support means passwordless authentication works across on-premises infrastructure, private cloud, public cloud, hybrid environments, and legacy systems that cannot be easily modernized.
Deployment Timeline: Typical enterprise implementations follow a 90-180 day timeline from initial deployment to full production rollout. The first 30 days cover planning, infrastructure setup, and pilot group deployment, typically IT staff and security team members. Days 30-90 expand to high-priority populations and critical systems. Days 90-180 complete organization-wide deployment. Larger enterprises with 10,000+ users may extend timelines to 6-12 months to manage change management and ensure comprehensive testing across all application integrations.
The Authentication Transition
The cybersecurity industry is experiencing a fundamental shift away from password-based authentication. Industry analysts, security frameworks, and regulatory bodies increasingly recognize that passwords cannot be secured through policy or technology enhancements. They must be eliminated. This creates a market transition period where early adopters gain competitive and security advantages while laggards accumulate risk.
Industry Guidance: IBM’s Cost of Data Breach Report explicitly recommends adopting phishing-resistant authentication methods including passkeys and hardware tokens, stating that passwordless authentication “significantly reduces risk of credential abuse.” NIST SP 800-63B authentication guidelines prioritize phishing-resistant authenticators and deprecate knowledge-based authentication including passwords. The FIDO Alliance promotes passwordless standards that major technology vendors are implementing across platforms.
Insurance Market Pressure: Cybersecurity insurance carriers increasingly require multi-factor authentication and passwordless controls as conditions for coverage. Organizations experiencing credential-based breaches while using traditional passwords face coverage disputes, higher premiums, and potential policy non-renewal. Demonstrating passwordless authentication implementation provides evidence of security control maturity that satisfies underwriter requirements and may reduce insurance costs.
Competitive Security Posture: As credential breaches become public, customer trust erodes and competitive disadvantage emerges. Organizations can demonstrate to customers, auditors, partners, and regulators that they’ve eliminated the attack vector responsible for 38-49% of breaches. In vendor selection processes, especially for regulated industries, security posture has become a primary evaluation criterion. Passwordless authentication provides differentiation that influences customer decisions and partnership opportunities.
Regulatory Evolution: Financial services regulators are implementing guidance requiring phishing-resistant authentication for customer-facing systems and privileged access. Healthcare regulators scrutinize authentication controls in HIPAA compliance assessments. European data protection authorities evaluate authentication mechanisms under GDPR. Organizations that wait for explicit regulatory mandates will find themselves behind competitors who proactively eliminated password vulnerabilities.
Conclusion: Eliminating the Attack Vector
The data demonstrates an unambiguous pattern: stolen credentials dominate the threat landscape, accounting for more breaches than any other attack method. These credential-based breaches cost an average of $4.81 million, take 292 days to detect and contain, consume over $4 million annually in operational overhead, and cannot be prevented through user training or password policies because they exploit fundamental architectural vulnerabilities in password-based authentication.
Healthcare organizations averaging $10.93 million per breach, financial services at $5.90 million, and large enterprises spending $25.6 million on credential-related incidents face existential risk from continuing password dependence. The 71% year-over-year increase in credential attacks, combined with dark web marketplaces offering 1,000+ stolen credentials daily at $10 each, ensures this threat will intensify rather than diminish.
Eliminating usernames and passwords through zero-knowledge architecture removes this entire attack category. Device-bound authentication, distributed cryptographic key storage, and dynamic challenge-response mechanisms render credential theft, phishing, credential stuffing, and password-related operational burden obsolete. Organizations implementing passwordless authentication eliminate the #1 breach vector, recover millions in annual operational costs, achieve faster breach detection for remaining threats, and gain competitive advantage through demonstrable security superiority.
The question facing enterprises is no longer whether to eliminate passwords, but whether they can afford the delay while credential-based attacks continue accelerating. Every month of password dependence represents continued exposure to the dominant attack vector, accumulated operational waste, and increasing regulatory risk. Organizations that act now prevent becoming the next $4.8 million breach statistic.
Sources and References
All statistics in this report are sourced from authoritative cybersecurity research:
- IBM Security & Ponemon Institute: Cost of a Data Breach Report 2023-2024
- IBM Security X-Force: Threat Intelligence Index 2024
- Verizon: Data Breach Investigations Report (DBIR) 2023-2024-2025
- Identity Theft Resource Center: 2023 Data Breach Report
- Ponemon Institute: Cost of Insider Threats 2023
- Industry research on password management costs (BioConnect, Daon, Forrester Research)