eIDAS 2.0 & the EUDI Wallet: A Practical Guide for Enterprise IAM (2025–2027)
October 9, 2025 by Max Yakub
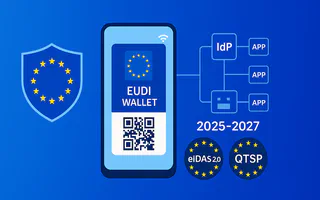
The European Union’s 27 member states are transforming digital identity with the European Digital Identity (EUDI) Wallet. The eIDAS 2.0 regulation (Regulation EU 2024/1183) entered into force on May 20, 2024, establishing the legal framework for wallet-based authentication and modernizing how businesses handle electronic identification and digital signatures across Europe.
What Does eIDAS Mean?
eIDAS stands for “electronic IDentification, Authentication and trust Services.” The original regulation (EU No 910/2014) took effect in 2016, establishing cross-border recognition of national eID schemes and qualified electronic signatures. However, adoption was fragmented with limited private sector uptake and no universal digital identity solution.
eIDAS 2.0 transforms this landscape by:
- Mandating that all member states issue standardized EUDI Wallets by late 2026
- Extending acceptance requirements to regulated private sector services and Very Large Online Platforms (VLOPs)
- Creating harmonized technical standards for verifiable credentials and selective disclosure
- Enabling mobile-first authentication and digital signatures with full legal validity
Key dates and obligations:
- May 20, 2024: eIDAS 2.0 regulation entered into force
- 2024-2025: Core implementing acts adopted defining technical standards
- Late 2026: Member states must provide at least one national EUDI Wallet (24 months after implementing acts)
- Late 2027: Regulated private services and VLOPs must accept EUDI Wallet upon user request (36 months after implementing acts)
The main goal of eIDAS 2.0 is to provide every EU citizen and business with a universal digital identity that works seamlessly for public services, private sector platforms, and cross-border transactions while maintaining user control, privacy, and GDPR data minimization principles.
What Is the European Digital Identity (EUDI Wallet)?
The EUDI Wallet is a mobile application that EU citizens and residents can install on their smartphone to securely store and present identity credentials, professional qualifications, educational certificates, payment information, and other verified attributes. The wallet gives individuals full control over their digital identity, enabling them to prove who they are and selectively disclose only the information needed for each transaction.
Main capabilities:
- User-controlled credentials: Puts identity data directly in users’ hands
- Qualified electronic attestations (QEAA): Qualified Trust Service Providers issue legally binding attestations across all member states
- Selective disclosure: Prove specific facts using SD-JWT without revealing underlying data
- Electronic signatures: Generate qualified signatures with same legal effect as handwritten
- Cross-border acceptance: Credentials work across all EU states
Workflow: User installs national wallet, receives credentials from government agencies and trust service providers, scans QR code when logging in, approves selective disclosure, and service receives cryptographic proof. For high-value transactions, users apply qualified electronic signatures directly from wallet.
Advantages: Reduced fraud through cryptographic security, faster onboarding without manual verification, lower compliance risk with built-in audit trails, better UX replacing passwords, and legal certainty with qualified signatures carrying full weight across EU states.
For IAM teams, the EUDI Wallet shifts the model from “store and verify” to “request and prove.” Solutions like WWPass are designed around this philosophy, with cryptographic identity architectures that eliminate shared secrets and enable phishing-resistant authentication flows aligned with wallet-based verification.
What eIDAS 2.0 changes, and why the EUDI Wallet matters
Wallet Fundamentals: Credentials, Attestations, and Selective Disclosure
With eIDAS 2.0, the EU strengthens personal data protection and security of digital transactions through three core mechanisms:
1. Verifiable credentials: Services request cryptographically signed credentials that prove attributes without requiring organizations to store sensitive databases, aligning with GDPR Article 5(1)(c) data minimization.
2. Qualified trust services: Qualified Trust Service Providers (QTSPs) issue QEAA with legal standing that can confirm professional status, educational credentials, or residency. These attestations are cryptographically signed and tamper-proof.
3. Selective disclosure: The eIDAS 2.0 Architecture Reference Framework (ARF) mandates wallet support for selective disclosure, allowing users to share only minimum necessary information. Technologies like SD-JWT and ISO 18013-5 mobile driving licenses enable privacy-preserving disclosure at scale.
Key security measures:
- Strong authentication with biometrics and device possession
- End-to-end encryption between wallet and relying party
- Revocation and lifecycle management for expired credentials
- Tamper-evident audit logging for accountability
For enterprise IAM architects, this means requesting attributes rather than collecting profiles. Platforms like WWPass already embrace this model with origin-bound authentication and selective attribute presentation that minimize stored PII.
Who Needs to Care: Public Sector, Regulated Industries, and VLOPs
Public sector: All government agencies and public services requiring online identification must accept the EUDI Wallet, including tax portals, healthcare platforms, and municipal services.
Regulated industries with strong authentication requirements: Private businesses (except micro and small enterprises) that use strong user authentication fall under scope:
- Financial services: Banks and payment providers under PSD2 Strong Customer Authentication requirements
- Telecommunications: Network operators and telecom providers
- Healthcare: Platforms handling sensitive health data
- Energy and utilities: Providers offering online account management
- Transport and mobility: Airlines, rail operators requiring identity verification
- Education: Universities using digital credentials for enrollment
Very Large Online Platforms (VLOPs): Under the Digital Services Act, platforms with over 45 million monthly active users in the EU must accept the EUDI Wallet when users voluntarily request it.
Cross-border businesses: Companies operating across multiple EU states benefit from automatic credential recognition, eliminating redundant verification processes.
For IAM teams in these sectors, deploying phishing-resistant solutions like WWPass MFA and passwordless SSO establishes the foundation for wallet integration as national implementations roll out in 2026-2027.
Electronic Signatures and Interoperability
eIDAS 2.0 advances electronic signature standardization through wallet-native signing, remote qualified electronic signatures (rQES) where QTSPs hold keys, and legal equivalence across all member states. Technical standards ensure signatures created with different wallets validate cross-border.
Organizations can replace paper-based processes with mobile-first signing for financial services, real estate contracts, healthcare consent forms, and legal documents. Platforms like DocuSign integrate with EUDI Wallet, while WWPass provides phishing-resistant authentication infrastructure.
Security Alignment, Phishing Resistance, and NIST AAL Mapping
Mapping Authentication Journeys to AAL2/AAL3
To operationalize eIDAS 2.0 with Zero Trust frameworks, classify digital identity journeys using NIST SP 800-63 Authenticator Assurance Levels.
AAL2 (phishing-resistant MFA): Requires cryptographic authenticators that resist verifier impersonation. Appropriate for most customer sign-ins and moderate-risk transactions. Achieved with:
- Passkeys (WebAuthn/FIDO2)
- Hardware security keys
- EUDI Wallet with biometric unlock
- WWPass cryptographic authentication
AAL3 (hardware-backed authentication): Demands non-exportable private keys in hardware secure elements. Use for:
- Privileged administrative actions
- High-value approvals (financial transfers, data exports)
- Regulatory scenarios requiring qualified signatures
- Access to classified or highly sensitive data
Practical mapping:
- Standard login (email, CRM, internal apps): AAL2 with passkeys or WWPass MFA
- Manager approvals: AAL2 with risk-based step-up
- Admin operations: AAL3 with hardware-backed keys
- Legal/financial transactions: AAL3 with qualified signatures from EUDI Wallet
Passwordless Authentication and Origin Binding
Modern phishing resistance eliminates shared secrets (passwords, OTPs) with cryptographic authenticators. Passkeys use cryptographic key pairs where private keys never leave devices, proving possession, binding to exact origin, resisting replay, and preventing phishing.
WWPass extends this with QR-mediated cross-device authentication via WWPass Key App, origin binding validation, zero-knowledge architecture, and hardware-backed keys for AAL3. Deploy passwordless as default, replacing VPN passwords with passkeys or WWPass for workforce SSO.
Integrating EUDI Wallets with Modern SSO and Identity Providers
OIDC/SAML Patterns for Wallet Credential Presentation
The eIDAS 2.0 ARF standardizes wallet interactions using OpenID for Verifiable Presentations (OpenID4VP), extending OpenID Connect to support verifiable credentials.
Integration flow:
- User initiates sign-in at relying party (RP)
- RP/IdP constructs OpenID4VP request specifying needed attributes
- User’s wallet displays requesting organization and attributes needed
- User approves selective disclosure, wallet generates verifiable presentation
- RP/IdP validates cryptographic signatures and issues OIDC/SAML session
Key considerations:
- Only request genuinely needed attributes (data minimization)
- Map wallet-derived claims to least-privilege roles
- Log transaction ID, requested/shared attributes, but avoid storing PII longer than necessary
Solutions like WWPass Passwordless SSO can broker wallet presentations alongside passkey authentication, providing unified policy enforcement.
Bridging Wallets and Passkeys: Cross-Device QR Authentication
QR-mediated authentication provides secure patterns for bridging EUDI Wallet interactions with existing infrastructure.
Cross-device flow:
- Desktop displays QR code with per-session challenge, origin, and nonce
- User scans with EUDI Wallet or passkey-enabled authenticator
- Wallet validates origin, presents credentials, signs challenge
- Desktop receives signed presentation and establishes session
Quishing (QR phishing) mitigation:
- Per-session QR with 60-90 second TTL
- Origin binding embedded in QR payload
- Visual trust indicators before credential presentation
- Cryptographic nonce prevents replay
For implementation patterns, see WWPass Authentication Guides, which outlines best practices for secure cross-device flows aligned with eIDAS 2.0 wallet interactions.
Device Signals and Risk Assessment
Augment wallet authentication with device posture (health, registration, hardware attestation), network signals (IP reputation, geolocation), and behavioral analytics. Apply risk-based step-up from AAL2 to AAL3 for privileged actions. WWPass provides device trust and cryptographic binding for risk engines.
Architecture Patterns with WWPass
Wallet-Ready Login Flows Using WWPass
Preparing infrastructure for EUDI Wallet acceptance starts with implementing phishing-resistant authentication today. WWPass offers a proven pathway aligned with wallet-based verification.
Deployment strategy:
- Phase 1 (Now-2025): Deploy WWPass MFA/SSO to eliminate passwords from high-risk accounts
- Phase 2 (2025-Early 2026): Extend passwordless to customer applications using QR-mediated cross-device flows
- Phase 3 (Late 2026-2027): Add EUDI Wallet acceptance as login option via OpenID4VP integration
Resources:
- WWPass Passwordless SSO for Web & Mobile Apps
- WWPass Multi-factor Authentication
- WWPass Key App for managing authenticators
QR Approvals That Resist Replay and Phishing
WWPass QR authentication addresses quishing threats through per-session nonces, origin binding, and short-lived challenges.
WWPass QR design principles:
- Unique QR per session tied to specific browser and relying party origin
- 60-90 second TTL with rotation on display
- Origin validation before credential presentation
- Server-generated nonce prevents replay attacks
- User confirmation with service name and logo
Combining with EUDI Wallet: QR flows can request both passkey authentication and wallet credential presentation in single interaction, achieving AAL3 assurance for PSD2 SCA scenarios while resisting social engineering.
Directed Identities and Minimizing Correlation
The EUDI Wallet supports per-relying-party pseudonyms, presenting unique identifiers to each service rather than global user IDs. WWPass implements similar origin-bound authentication where each relying party has unique relationship with user accounts.
Best practices:
- Avoid shared identifiers (email, phone) as primary keys
- Use attribute-based access control without storing unnecessary PII
- Federate identity with pairwise pseudonymous identifiers
For regulated signing requiring qualified electronic signatures, WWPass integrates with remote qualified signature services for mobile-first workflows meeting eIDAS 2.0 requirements.
Privacy, Consent, and User Experience

Selective Disclosure and Data Minimization
The EUDI Wallet operationalizes GDPR Article 5 data minimization using SD-JWT and ISO 18013-5 formats. Services request minimum attributes per transaction. Treat wallet as attribute source, not profile store.
Consent Prompts and Transparency
Under GDPR Articles 7 and 13, valid consent must be freely given, specific, informed, and easily withdrawn. Wallet prompts must clearly explain what’s requested, who’s asking, and why. Design requirements include naming the relying party, listing requested attributes, explaining purpose and retention, providing equal “Share” and “Decline” options, and enabling one-tap withdrawal.
Accessibility and Language Support
Wallet acceptance must meet WCAG 2.2 and EN 301 549 standards. Critical requirements include:
- No cognitive function tests (CAPTCHAs) for authentication
- Visible focus indicators for keyboard navigation
- Clear error messages with resolution instructions
- Sufficient touch targets (44x44 CSS pixels)
- Screen reader compatibility and language localization
Implementation Blueprint (90-Day Plan)
Readiness Assessment
Map your wallet-relying party surface: customer portals, partner channels, workforce apps with strong authentication. Inventory IdP capabilities for OIDC/SAML brokering, attribute governance, and OpenID4VP verifier support.
Baseline priorities:
- Verify IdP can request minimal claims and map to roles
- Update privacy impact assessments for verifiable credentials
- Validate SIEM can capture wallet transaction logs
Deploy WWPass components for phishing-resistant foundation:
- WWPass Passwordless SSO
- WWPass MFA
- WWPass Key App
Pilot Wallet Acceptance
Choose low-impact journey (age verification, account proofing) to maximize feedback. Present QR-to-wallet flow with selective disclosure, hardened against quishing with per-session challenges and origin binding.
Metrics to track:
- Wallet acceptance rate vs. legacy MFA
- Selective disclosure approval/decline patterns
- Time-to-complete authentication
- Help desk contacts per 1,000 logins
Governance and Audit Trails
Establish joint product-security-privacy working group to oversee wallet integration. For each transaction, log: requesting RP, attributes requested/shared, timestamp, assurance level, consent status, and transaction IDs.
Provide user-visible history in wallet and server-side tamper-evident logs for auditors, aligning with GDPR accountability, PSD2 SCA evidence requirements, and NIS2 incident reporting.
Compliance Mapping and Audits

GDPR, PSD2 SCA, and NIS2 Alignment
GDPR: Selective disclosure demonstrates data minimization (Article 5(1)(c)). Wallet transaction logs support user rights (access, rectification, erasure) and accountability.
PSD2 SCA: Under Article 97, banks must apply strong customer authentication. EUDI Wallet combines possession (device), inherence (biometric), and dynamic linking for compliance.
NIS2: Directive (EU) 2022/2555 requires risk management measures including strong authentication. Wallet-based authentication reduces account takeover risk and provides provable audit trails.
Logging Requirements for Regulators
Implement standard event taxonomy capturing: requesting RP, attributes requested/shared, timestamp, assurance level, consent status, transaction IDs, device signals, and network context.
Retain operational logs for 90 days to 1 year; compliance evidence per regulatory requirements (PSD2: 5 years). Set SLAs for providing evidence to auditors (24-48 hours) and rehearse trace-back drills quarterly.
Vendor Selection for Wallet-Ready IAM
When procuring identity solutions, require:
- OpenID4VP verifier support with published conformance results
- OIDC/SAML brokering and selective disclosure policy mapping
- WCAG 2.2 / EN 301 549 conformance documentation
- Short-TTL QR, origin binding, replay resistance
- SIEM-ready structured logs
Prefer vendors with proven passwordless deployments and clear wallet integration roadmaps. WWPass provides ready-to-deploy components with phishing-resistant architecture that naturally extends to wallet verification.
FAQs
Do we need to accept EUDI Wallets by 2026 or 2027?
Member states must provide wallets by late 2026 (24 months after implementing acts). Enterprise acceptance obligations begin 36 months after, placing most deadlines in late 2027. Plan pilots in 2025-2026 for readiness.
How do wallets differ from passkeys and smart cards?
EUDI Wallet stores verifiable credentials proving who you are and what attributes you have. Passkeys prove you’re present now with phishing-resistant authentication. Smart cards provide hardware credentials for signing and regulated contexts. Use wallets for identity/attributes, passkeys for everyday login, smart cards for qualified signatures.
What’s minimum for “phishing-resistant” under NIST? NIST SP 800-63B AAL2 requires cryptographic authenticators with origin binding (passkeys, WWPass, EUDI Wallet with biometrics). AAL3 adds hardware-backed keys with non-exportable private keys. Use origin-bound methods as default; escalate to AAL3 for admin and high-impact transactions.
About WWPass WWPass provides phishing-resistant authentication solutions that align naturally with eIDAS 2.0 wallet requirements. Learn more at wwpass.com or contact info@wwpass.com.