MFA: Why Quality Beats Quantity
February 21, 2018 by Perry Chaffee

Bill Gates might’ve declared the password dead back in 2014. However, at last year’s Black Hat Cybersecurity Conference, the chief information security officer of Facebook told the world that passwords were one of the biggest problems companies’ faced. Yet, Security Week estimates that there are more than 90 billion passwords, and they are multiplying quickly. The truth is, human readable credentials (HRC) like passwords are listed as one the leading causes (more than 81 percent according to the Verizon Data Breach Investigations Report) of data breaches and identity thefts.
In response to all this, companies are adopting two factor authentication (2FA) and multi-factor authentication (MFA). The reality? These are Band-Aid approaches to a fundamentally obsolete approach. Passwords and usernames are frustratingly inconvenient, and most 2FA and MFA just add an additional layer of inconvenience to hurt the user experience even more. Worse yet, the most common approach to 2FA involves sending a code by text messages over SMS - yet the National Institute of Standards and Technology recommends against this approach because it’s not secure either. Google observed that nearly 1 in 5 of phishing kits collect phone data in order to intercept these codes. Google also noted that less than 10 percent of their user base even bothers to turn 2FA on – the other 90 percent are protected only by passwords.
With data breaches constantly in the headlines and identity theft costing U.S. consumers $15 billion annually, it’s time for businesses to take a different approach. We can start by asking ourselves the obvious question - if our first factor is so bad that we need a second factor, then why are we still using the first factor at all? While passwords unfortunately aren’t dead yet, they are certainly obsolete, as well as HRC, such as usernames, personal identifying information, and answers to security questions. Any information that can be entered into a form field by one person could also be entered by a hacker who has somehow obtained it without the knowledge of their victim.
To successfully protect our data, organizations and users, we need a paradigm shift which switches the first step in the login process from “something you know” to “something you have.” This right-factor authentication (RFA) could take the form of something users already have -like their phone, it could also be in the form of a smartcard ID or USB keyset, or even other wearables like rings, watches or implants. This dramatically reduces the risk of compromise, because hackers can’t even try accessing an account without first stealing this physical item. Even if they do, they can still be stopped if additional verification steps request biometrics like fingerprints or even a PIN known only to the user (similar to a debit card).
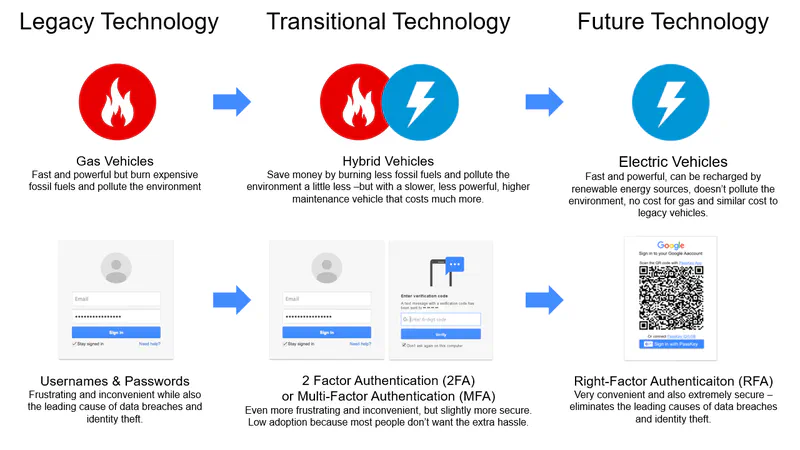
This shift from traditional 2FA and MFA may seem subtle, but it’s critically important. To put it in perspective, let’s compare the shift from passwords to RFA with the world’s transition from gas powered vehicles to electric vehicles.
Authentication and transportation both started off with legacy technology. Cars had gas powered engines, while authentication depended on passwords and usernames. Over time, problems with gas powered engines motivated people to start seeking electric alternatives. Because battery storage wasn’t ready yet, people were willing to compromise with hybrid vehicles, which basically combined the worst parts of both. These vehicles still depended on burning gas, and although they also had electric engines, the overall outcome was not ideal. Similarly, as problems with passwords became widespread, many vendors emerged selling solutions to augment them, once again combining the worst parts of both. Just as better battery technology allows companies like Tesla to produce supercars with no dependence on gas, WWPass technology provides superior convenience and security, with no dependence on passwords.
How do your multi-factor solutions stack up? Get the facts and avoid mistakes when upgrading your systems.