Zero-Knowledge Authentication for Regulated Industries
February 17, 2026 by Nick Morgan

Introduction
Regulated industries are hemorrhaging money through credential-based breaches. The numbers paint a stark picture of an authentication crisis that traditional security measures have failed to solve.
The Cost of Credential Vulnerabilities:
| Industry | Average Breach Cost |
|---|---|
| Financial Services | $5.90M |
| Pharmaceuticals | $4.78M |
| Energy | $4.78M |
| Industrial | $4.45M |
Beyond these staggering breach costs, credential-based attacks have become the primary threat vector. In financial services alone, stolen credentials and ransomware each account for 30% of successful breaches, while Business Email Compromise scams have transferred $6.3B in a single year. Traditional multi-factor authentication only adds layers to fundamentally broken systems; it doesn’t eliminate the credentials that attackers target.
Zero-knowledge authentication takes a different approach entirely. Rather than protecting passwords with additional security layers, it eliminates both usernames and passwords from the authentication process. This fundamental shift addresses the root cause of credential-based breaches across financial services, pharmaceutical, energy, and industrial sectors.
Why Credential-Based Authentication Fails in High-Stakes Environments
The Financial Services Credential Crisis
Financial services organizations face a perfect storm of credential-based threats. Understanding the specific attack patterns helps clarify why traditional approaches continue to fail despite significant security investments.
Primary Attack Vectors:
- Stolen credentials - 30% of confirmed breaches
- Ransomware attacks - 30% of confirmed breaches
- Business Email Compromise - $6.3B transferred annually
- Phishing campaigns - Harvesting credentials through fake login pages
- Social engineering - Manipulating users into revealing passwords
These attacks succeed because passwords create a persistent vulnerability. No matter how complex the password policy or how sophisticated the MFA implementation, credentials remain stealable, guessable, and reusable once compromised.
How Credentials Get Compromised
Attackers don’t need to be exceptionally sophisticated to steal credentials. Multiple proven techniques give them numerous paths to compromise:
Common Credential Theft Methods:
| Attack Method | How It Works | Why It Succeeds |
|---|---|---|
| Phishing | Fake login pages harvest credentials | Users can’t distinguish legitimate from fake |
| Infostealer Malware | Captures passwords from infected devices | Credentials stored in browsers and applications |
| Brute Force | Automated password guessing | Weak or predictable passwords remain common |
| Dark Web Purchase | Buying stolen credential databases | One breach compromises multiple systems via reuse |
| Insider Threats | Authorized users misuse legitimate access | Passwords provide no distinction between legitimate and malicious use |
The Hidden Costs Beyond Breach Expenses
Even organizations that avoid major breaches waste substantial resources managing password-based authentication systems. These operational costs compound year after year without delivering actual security improvements.
Ongoing Password Management Costs:
- Help desk burden - Password reset requests consume IT resources constantly
- Security training - Repeated awareness programs attempting to change user behavior
- Compliance overhead - Documenting password policies for regulatory audits
- Tool licensing - Password managers, rotation tools, complexity enforcers
- User productivity loss - Time wasted on password resets and authentication friction
Why Regulated Industries Can’t Afford Weak Authentication
Each regulated sector faces unique threats that make credential vulnerabilities particularly dangerous. Understanding these sector-specific risks clarifies why passwordless authentication for financial services and other regulated industries has become critical.
Financial Services: The direct connection to money makes financial institutions prime targets. Compromised credentials provide immediate access to funds, customer accounts, and sensitive financial data. Regulatory frameworks like PCI DSS, GDPR, and PSD2 impose strict authentication requirements, while customer trust erosion after breaches creates long-term revenue impacts beyond immediate breach costs.
Pharmaceutical: Research and development investments worth billions are protected by authentication systems. Clinical trial data, proprietary formulations, and regulatory submissions require maximum security. Patient privacy regulations add compliance complexity, while corporate espionage from competitors and foreign actors makes intellectual property a constant target.
Energy: Critical infrastructure attracts nation-state attackers with resources far beyond typical cybercriminals. SCADA and control systems require authentication that prevents operational disruption with public safety implications. Regulatory oversight of security practices means breaches trigger both operational and compliance consequences.
Industrial: Manufacturing processes, proprietary designs, and supply chain systems contain valuable intellectual property. Competitors and foreign intelligence services target trade secrets, while supply chain disruptions can cascade across entire industries. Authentication weaknesses create espionage opportunities with competitive implications.
How Passwordless Authentication for Financial Services Eliminates Attack Vectors
Zero-Knowledge Architecture Fundamentals
Zero-knowledge authentication doesn’t just strengthen credential-based systems, it eliminates credentials entirely. Understanding what gets removed versus what replaces traditional authentication clarifies the security transformation.
What Zero-Knowledge Authentication Eliminates:
| Removed Element | Security Impact |
|---|---|
| Usernames | No identifier to correlate across services |
| Passwords | Nothing to steal, phish, or crack |
| Password databases | No honeypot attracting attackers |
| Password reset workflows | No social engineering attack vector |
| Credential storage | No central point of compromise |
What Replaces Traditional Credentials:
| New Component | Function |
|---|---|
| WWPass Key | Hardware token, smart card, or mobile app with cryptographic capabilities |
| Non-human-readable credentials | Transaction-specific data useless if intercepted |
| Device-based cryptography | All operations on user’s device, never centralized |
| Distributed data storage | Encrypted fragments across 12 certified nodes |
| Protected User Identifier | Unique identifier per service, cannot be correlated |
How the Technology Actually Works
The technical implementation determines whether passwordless authentication for financial services actually delivers security improvements or simply relocates vulnerabilities.
Device-Based Cryptographic Operations:
All cryptographic operations happen on the WWPass Key itself, whether that’s a mobile app, smart card, or hardware token. The system never sees credentials, encryption keys, or personal data. Master encryption keys never leave the user’s device, even during authentication. If a user loses or damages their key, restoration happens without administrator intervention through the distributed architecture, not through password resets that create security gaps.
Distributed Data Storage Architecture:
Data encryption happens client-side before fragmentation across 12 certified nodes using Reed-Solomon architecture. No single server contains enough information to reconstruct user data, attackers would need to compromise multiple nodes simultaneously plus the user’s device. Even a compromised node yields only encrypted fragments useless without the other components. This distributed approach eliminates the centralized databases that make credential-based systems attractive targets.
Non-Human-Readable Credentials:
Each authentication transaction generates fresh cryptographic data specific to that session. These credentials cannot be reused even if intercepted through network monitoring or man-in-the-middle attacks. Unlike passwords that retain value after theft, non-human-readable credentials have no utility outside their specific transaction context. This makes credential harvesting pointless, attackers get data they cannot exploit.
Stopping Specific Financial Services Attacks
Understanding how zero-knowledge authentication blocks real-world attack patterns demonstrates practical security value beyond theoretical improvements.
Credential Stuffing Prevention:
Traditional defense: Rate limiting, CAPTCHA, behavioral analysis Zero-knowledge solution: No reusable credentials exist to stuff into login forms
Credential stuffing attacks rely on stolen username/password pairs from one breach being tested against other services. When credentials don’t exist in the authentication process, stuffing attacks have nothing to work with. Each authentication requires the physical WWPass Key plus optional biometric or PIN, attackers cannot replicate this without stealing the physical device.
Account Takeover Protection:
Traditional defense: Password complexity, MFA, anomaly detection Zero-knowledge solution: No passwords to steal, guess, or crack
Account takeover typically begins with compromised credentials obtained through phishing, malware, or purchase. Zero-knowledge authentication eliminates this initial access vector entirely. Phishing campaigns cannot harvest credentials that don’t exist. Social engineering targeting passwords becomes irrelevant when the authentication system doesn’t use passwords.
Business Email Compromise Defense:
Traditional defense: Email authentication protocols, user training, wire transfer procedures Zero-knowledge solution: Email account access requires physical device possession
BEC attacks transferred $6.3B by compromising executive email accounts through credential theft. When email system authentication requires the physical WWPass Key, remote attackers cannot access accounts even with stolen passwords. The authentication architecture forces attackers toward much more difficult physical device theft rather than remote credential compromise.
Ransomware Initial Access Prevention:
Traditional defense: EDR, network segmentation, backup systems Zero-knowledge solution - Eliminates credential theft vector used in 30% of attacks
Ransomware attacks frequently begin with stolen credentials providing initial network access. By eliminating credentials as an attack vector, zero-knowledge authentication forces attackers toward more difficult exploitation methods like zero-day vulnerabilities. This significantly raises the cost and complexity of successful attacks, pricing out less sophisticated threat actors.
Benefits for Regulated Industries Beyond Finance
Pharmaceutical Research Protection:
Clinical trial data and proprietary research require authentication that protects intellectual property worth billions while maintaining compliance with patient privacy regulations. Zero-knowledge architecture ensures researcher access without password vulnerabilities that could expose patient data or formulations to competitors or foreign actors.
Energy Infrastructure Security:
SCADA system access and critical infrastructure control demand maximum authentication strength against nation-state threats. Zero-knowledge authentication provides phishing-resistant access to operational systems while maintaining emergency access protocols that ensure operational continuity during crisis situations.
Industrial IP Protection:
Supply chain platforms and engineering systems contain trade secrets and manufacturing processes. Authentication that isolates each service through Protected User Identifiers prevents credential compromise in one system from cascading to others, limiting espionage damage even if attackers succeed against individual targets.
Meeting Compliance Requirements for Passwordless Authentication Financial Services

PCI DSS Compliance for Financial Services
Payment Card Industry Data Security Standard imposes specific authentication requirements that zero-knowledge architecture meets while exceeding minimum compliance thresholds.
PCI DSS Requirement 8 (Access Control):
| PCI DSS Requirement | Traditional Approach | Zero-Knowledge Solution |
|---|---|---|
| Unique user identification | Username assignment | Protected User Identifier per service |
| Multi-factor authentication | Password + second factor | Inherent multi-factor (possession + optional biometric) |
| Password complexity | Policy enforcement | No passwords exist |
| Password rotation | Quarterly changes | No passwords to rotate |
The compliance advantage extends beyond checkbox requirements. Automated compliance reporting provides auditors with complete authentication event trails. Reduced compliance scope comes from credential elimination, no passwords mean no password policy violations. Quarterly compliance validation simplifies when the architecture prevents entire categories of violations.
PCI DSS Requirement 3 (Data Protection):
Client-side encryption keeps cardholder data encrypted before transmission. Non-human-readable credentials meet encryption standards without additional implementation. Distributed storage prevents single point of compromise that could expose multiple cardholder records. Zero-knowledge architecture eliminates scenarios where administrators or system compromises expose unencrypted payment data.
NIST 800-63 Phishing-Resistant Authentication
Federal and enterprise authentication standards define specific technical requirements for phishing resistance that zero-knowledge authentication satisfies inherently.
Authenticator Assurance Level 3 (AAL3) Requirements:
- Hardware-based authentication - WWPass Key provides cryptographic device
- Phishing resistance - No credentials exist to harvest through fake login pages
- Verifier impersonation resistance - Cryptographic binding prevents man-in-the-middle
- Multi-factor authentication - Possession (device) plus optional inherence (biometric) or knowledge (PIN)
Digital Identity Guidelines compliance extends to federation protocols (SAML, OIDC), privacy requirements through zero-knowledge design, authenticator lifecycle management with user self-service, and authentication assurance appropriate for high-value financial transactions.
Financial Regulatory Standards
Strong Customer Authentication (SCA) under PSD2:
European banking regulations require specific authentication elements that zero-knowledge architecture provides inherently:
- Possession factor - WWPass Key device
- Inherence factor - Optional biometric or knowledge factor (PIN)
- Dynamic linking - Transaction-specific authentication data
- Independence - Breach of one factor doesn’t compromise others
This exceeds European banking authentication requirements while simplifying compliance documentation for financial institutions operating across multiple jurisdictions.
GDPR Data Protection:
Data minimization through zero-knowledge architecture means systems don’t collect or store unnecessary personal data. Encryption at rest and in transit protects data throughout its lifecycle. Right to erasure simplifies when no centralized credential storage exists. Privacy by design principles are built into the foundation rather than added as compliance afterthoughts.
Cross-Industry Compliance Frameworks
CMMC for Defense Contractors:
Defense contractors in regulated industries face Cybersecurity Maturity Model Certification requirements:
| CMMC Level | Requirement | Zero-Knowledge Solution |
|---|---|---|
| Level 2 | Multi-factor authentication | Inherent in architecture |
| Level 3 | Phishing-resistant authentication | No phishable credentials exist |
| Level 2/3 | Access control with least privilege | Per-service Protected User Identifiers |
| Level 2/3 | Incident detection and response | Complete authentication audit trail |
SOC 2 and ISO 27001:
Third-party certification support comes from security controls documentation that maps directly to zero-knowledge architecture components. Access control requirements are exceeded through credential elimination rather than just met through policy. Regular penetration testing validates that eliminated attack vectors remain closed.
Key Management Standards:
NIST key management recommendations guide the distributed architecture implementation. Segregation of roles with split knowledge ensures no single administrator controls all components. Dual control for sensitive operations prevents insider threats. Administrator access separated from data access means system managers cannot view unencrypted sensitive information.
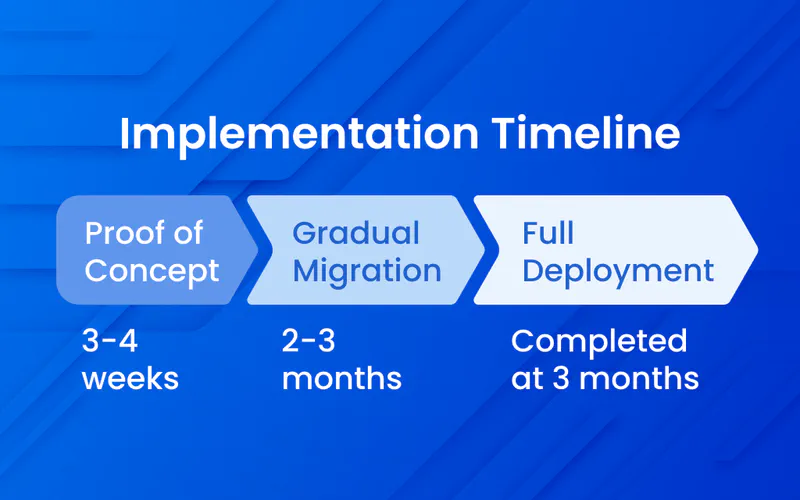
Real-World Implementation: 3-Month Timeline
Case Study: SaaS Document Management Platform
A document management company serving regulated industries implemented zero-knowledge authentication with measurable results that demonstrate practical viability beyond theoretical benefits.
Implementation Timeline and Approach:
| Phase | Duration | Activities | Results |
|---|---|---|---|
| Proof of Concept | 3-4 weeks | Integration testing, user pilot | Successful authentication validation |
| Gradual Migration | 2-3 months | Coexistence with legacy, user adoption | Growing adoption, ticket reduction |
| Full Deployment | Completed at 3 months | Legacy decommission | Zero password tickets, compliance achieved |
Migration Strategy:
Existing users bound their WWPass Key to current accounts without recreating user databases or forcing account resets. New users onboarded directly with passwordless authentication, experiencing only the secure system. The incentivized phase offered passwordless alongside legacy authentication, allowing users to experience benefits before mandate. The mandatory phase decommissioned legacy credentials only after organization-wide adoption eliminated business continuity risks.
Measured Business Outcomes:
Password-related support tickets eliminated completely from significant IT burden to zero incidents. User satisfaction improved significantly as friction decreased and security strengthened simultaneously. Compliance posture achieved GDPR requirements while becoming resistant to insider threats. IT burden reduced through self-service key management that eliminated administrator intervention for routine access issues.
Financial Services Applications
Banking and Investment Platforms:
- Online banking portals with phishing-resistant access for retail customers
- Mobile banking apps with seamless authentication across iOS and Android
- Trading platforms requiring transaction authorization for high-value trades
- Investment portals with regulatory compliance built into architecture
Back-Office and Operations:
- Wire transfer authorization with separation of duties preventing single-person fraud
- Regulatory reporting systems with complete audit trails for examiner review
- Compliance documentation platforms protecting sensitive regulatory filings
- Executive access with enhanced security controls for privileged operations
Customer-Facing Services:
- Account opening and onboarding workflows without password creation friction
- Self-service portals for account management reducing call center load
- Mobile payment authentication providing security and convenience
- Third-party fintech integrations with isolated authentication per service
Regulated Industry Use Cases
Pharmaceutical:
Clinical trial data management systems protecting patient privacy and research integrity. Research collaboration platforms enabling secure multi-institution projects. Regulatory submission portals for FDA and international agency filings. Manufacturing execution systems controlling production of controlled substances.
Energy:
SCADA and infrastructure control access preventing unauthorized operational changes. Remote operations monitoring for distributed generation and transmission. Emergency response systems maintaining access during crisis situations. Maintenance and contractor authentication with temporary access controls.
Industrial:
Product lifecycle management systems protecting designs from concept through production. Supply chain coordination platforms with partner access isolation. Engineering design and CAD systems containing proprietary innovations. Quality control and testing access with traceability requirements.
Technical Integration
Compatibility with Existing Infrastructure:
| Protocol | Purpose | Integration Benefit |
|---|---|---|
| SAML 2.0 | Single sign-on | Works with existing enterprise SSO |
| OIDC | Modern app authentication | Supports cloud and mobile applications |
| OAuth2 | API authorization | Enables third-party integrations |
| RADIUS | Network access control | Authenticates VPN and wireless access |
| LDAP/AD | Directory services | Synchronizes with user databases |
| Kerberos | Legacy systems | Supports older applications |
Deployment Flexibility:
Works alongside existing IAM infrastructure without replacement requirements. No forced rearchitecture of authentication systems reduces implementation risk. Gradual migration allows testing and validation at each stage. Coexistence with legacy systems during transition maintains business continuity.
Form Factor Options:
| Form Factor | Use Case | User Benefit |
|---|---|---|
| Mobile app (iOS/Android) | General workforce | Device already carried daily |
| Smart card | High-security environments | Familiar form factor for regulated settings |
| USB+NFC fob | Workstation access | Works with desktop and mobile devices |
| Multiple devices per user | Redundancy | Backup access without administrator help |
Implementation Roadmap: Three-Phase Deployment Strategy
Phase 1: Proof of Concept (3-4 Weeks)
The first phase validates technical feasibility and builds organizational confidence in the solution before broader rollout.
Objectives:
- Confirm integration with existing authentication infrastructure
- Validate compliance with applicable regulatory frameworks
- Measure user adoption and satisfaction in controlled environment
- Document measurable improvements in support burden
Activities and Success Criteria:
| Activity | Success Criteria |
|---|---|
| Select pilot group (10-50 users) | Representative cross-section of roles and systems |
| Integrate via SAML/OIDC | Successful authentication to all tested applications |
| Test critical application workflows | No functionality loss, improved user experience |
| Validate compliance requirements | Security team confirmation of PCI DSS, NIST 800-63, GDPR alignment |
| Collect user feedback | Positive satisfaction scores, identified edge cases addressed |
| Measure baseline metrics | Documented reduction in password-related support tickets |
Phase 2: Gradual Migration (2-3 Months)
Expansion across the organization while maintaining operational stability and building compliance documentation.
Objectives:
- Achieve broad organizational adoption through incentives
- Maintain business continuity throughout transition
- Build comprehensive compliance documentation
- Prepare for legacy system decommissioning
Activities and Tracking:
| Activity | Metric to Track |
|---|---|
| Offer passwordless alongside legacy | Adoption rate percentage weekly |
| Bind WWPass Keys to existing accounts | Account migration completion rate |
| Expand to additional departments | Department-by-department rollout status |
| Monitor support ticket trends | Weekly ticket volume by category |
| Train administrators | Administrator competency assessments |
| Collect compliance documentation | Audit-ready documentation completeness |
| Address edge cases | Exception resolution rate |
| Plan legacy shutdown timeline | Detailed decommissioning schedule |
Success Indicators:
Adoption rate trends showing consistent growth toward majority usage. Support ticket volume reduction demonstrating operational improvements. Authentication success rates maintaining or exceeding legacy system reliability. User satisfaction scores increasing as passwordless becomes default experience. Compliance documentation completeness enabling audit readiness.
Phase 3: Full Deployment
Final transition to passwordless-only authentication and realization of complete benefits.
Objectives:
- Mandate passwordless authentication across entire organization
- Decommission legacy credential infrastructure completely
- Achieve full compliance posture across all frameworks
- Establish ongoing optimization and monitoring processes
Activities and Outcomes:
| Activity | Expected Outcome |
|---|---|
| Mandate passwordless for all users | 100% adoption, legacy disabled |
| Disable legacy authentication | Password databases decommissioned |
| Remove password infrastructure | IT infrastructure simplification |
| Document compliance achievement | Full PCI DSS, NIST 800-63, GDPR compliance |
| Calculate total cost savings | ROI documentation for stakeholders |
| Establish continuous monitoring | Ongoing security and compliance validation |
| Schedule regular security assessments | Penetration testing and vulnerability scanning |
| Optimize based on feedback | User experience improvements |
Final Results:
Complete elimination of password-related support tickets saves IT resources continuously. Near-zero credential-based phishing attack surface reduces security incidents. Audit readiness across all applicable frameworks simplifies regulatory examinations. Measurable ROI from reduced IT overhead justifies initial implementation investment. Improved user productivity and satisfaction creates organizational benefits beyond security. Competitive advantage in regulated markets attracts customers prioritizing security and compliance.
Conclusion: The Business Case for Zero-Knowledge Authentication
The financial case for eliminating credential-based authentication in regulated industries is straightforward. Financial services organizations face $5.90M average breach costs, with 30% of attacks exploiting stolen credentials or ransomware. Traditional password-based systems, even with multi-factor authentication, create persistent vulnerabilities that sophisticated attackers exploit successfully and repeatedly.
Zero-knowledge authentication removes credentials from the attack equation entirely. By eliminating both usernames and passwords, the technology addresses the root cause rather than adding protective layers around fundamentally compromised architecture. The 3-month implementation timeline from proof of concept to full deployment demonstrates that transformation doesn’t require multi-year projects or business disruption.
Organizations implementing passwordless authentication for financial services achieve multiple simultaneous benefits: credential attack vector elimination, regulatory compliance across PCI DSS, NIST 800-63, and GDPR, operational cost reduction through eliminated password support, and competitive differentiation in markets where security drives customer decisions.
Pharmaceutical, energy, and industrial sectors gain the same foundational security protecting proprietary research, critical infrastructure, and intellectual property. The zero-knowledge architecture adapts to sector-specific requirements while maintaining the core security benefit: attackers cannot steal, guess, or phish credentials that don’t exist.
Compliance transforms from checkbox requirement to competitive advantage. When authentication architecture prevents entire categories of violations and attacks, regulatory examinations become demonstrations of security leadership rather than searches for vulnerabilities. The technology foundation supports business growth into regulated markets while reducing the operational overhead that credential-based systems impose.