Mobile SSO Risks & WWPass Protection
February 18, 2020 by Daniel Waldman

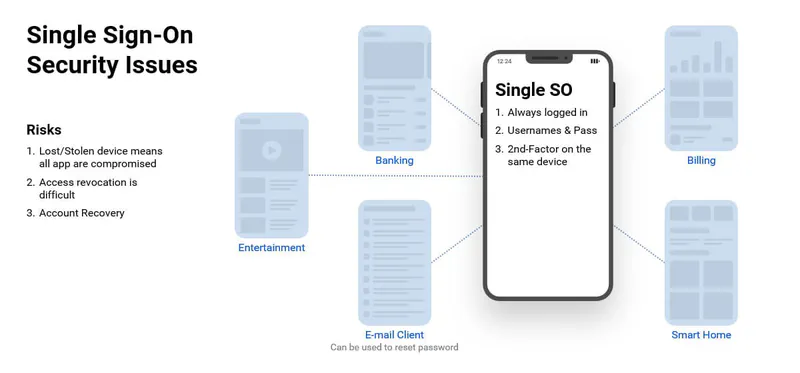
Single sign-on (SSO) has become a popular feature within corporate infrastructures, enabling users to quickly bypass typical security checks to get to applications. In fact, it’s become common for employees to use SSO along with their personal smartphones to log in to corporate applications. However, this scenario has some major security challenges that, if left unchecked, can spell disaster should someone get a hold of employees’ phones.
The top concern anyone should have about their smartphone is whether or not they’re protected should a thief or hacker gain access to their phone. Unauthorized access can happen if the device is stolen and hacked, or if a hacker gains access by remotely exploiting device software/operating system vulnerabilities. When an SSO system is deployed in the corporate infrastructure, the attacker gets instant access to all ecosystem applications used on a particular device.
For example, email client applications are commonly left open and the user is always logged in on smartphones, which makes the situation highly dangerous. An attacker can not only gain access to sensitive information in the email messages, but also use the victim’s email account to perform password resets. In such cases, SMS or push-based second factors are useless as well because the attacker is able to receive verification codes on the compromised device.
How WWPass Multi-factor Authentication Can Help Protect Enterprise Applications
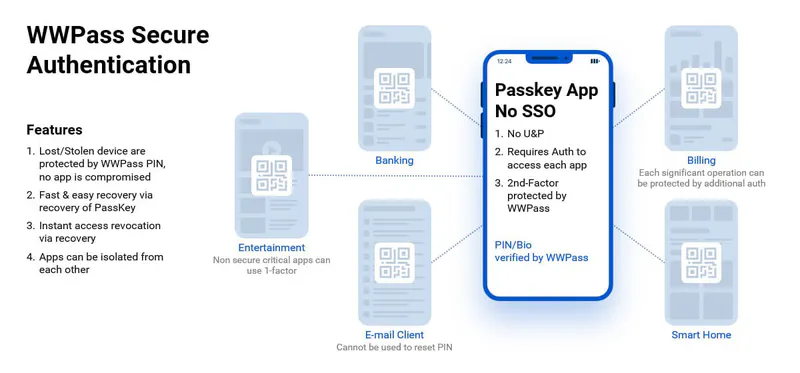
To protect enterprise applications within an SSO ecosystem, it is highly recommended to use multi-factor authentication (MFA), where one of the factors is not already present or accessible on the mobile device. This type of system can actually save time in environments that require frequent re-authentication to applications.
Authentication with WWPass Key (mobile app) is much more straightforward and less time-consuming than traditional authentication with usernames and passwords, as well as authentication using usernames, passwords, and any 2nd factor. Using WWPass, there is no need to type in usernames, email addresses, long passwords and such, all of which can waste a huge amount of the user’s time. What’s more, WWPass doesn’t use SMS-based 2nd factors, so the user doesn’t have to wait for the notifications to arrive.
Instead, WWPass typically only requires users to tap the authentication QR code and enter their PIN or use biometrics (i.e. fingerprint). The whole process is considerably faster than username and password-based authentication, but it’s also more secure. This allows users to perform authentication more frequently (e.g. authenticate each app separately) and implement even more sophisticated authentication schemes while providing a user-friendly experience. It is not only faster and easier to use, but also it is safer because it allows the user to authenticate quickly each time the app is launched. This approach minimizes the number of applications remaining in the “logged in” state on the smartphone, thus reducing what an attacker can access if the user’s device is stolen or compromised.
Second, WWPass does not verify or store PINs on user smartphones. PIN verification is handled by the WWPass network. WWPass network employs the Secure Remote Password (RFC 2945) protocol, which guarantees that no PIN-equivalent data is stored on the WWPass servers. WWPass network has a built-in anti-brute-force mechanism, which makes brute-force or wordlist-based attacks on PINs impractical.
In situations when the user’s smartphone is under the attacker’s control, the attacker still needs to “guess” the PIN to be able to log into an app. With traditional password-based authentication, the attacker just resets the password using the user’s email, but by eliminating the need for email/password logins, WWPass makes it practically impossible for the attacker to log into applications on the user device.
Third, unlike traditional authentication solutions that rely solely on emails for account recovery, WWPass features a smarter approach to help prevent hackers from gaining access to protected apps. To recover access to WWPass Key (mobile app), the user must not only have access to the email used to back up WWPass Key but also know the PIN, which cannot be reset by email. Although the attacker is likely to have access to the user’s email, only the user can restore their WWPass Key using their PIN and can permanently block WWPass Key on the device controlled by the attacker.
Last but not least, WWPass Key stores all cryptographic secrets in a hardware backed-up cryptographic storage on the user device (e.g. iOS Keychain). In the past, some attacks lead to keychain information extraction. But as of today, hardware backed-up keychains are almost as secure as smartcards.
Summary:
- WWPass does not recommend using single sign-on (SSO) on mobile devices for security reasons;
- WWPass offers a straightforward login user experience, which provides a higher level of security by implementing more sophisticated multi-factor authentication schemes;
- WWPass PIN verification is resistant to brute-force and wordlist-based attacks, and the WWPass PIN cannot be reset via email;
- Recovering WWPass PassKey app requires PIN, which protects the PassKey when the attacker can access the recovery email;
- The way WWPass PassKey stores cryptographic secrets is not vulnerable to the vast majority of attacks.