Zoom’s Biggest Security Issue Explained
May 18, 2020 by Daniel Waldman

Thanks to the global Covid-19 pandemic, Zoom has become the top video call service, growing to a massive 300 million users since the start of the outbreak. Of course, this growth has revealed a number of security issues, least of which is “zoom bombing,” where strangers jump into meetings uninvited.
In response to the criticism it’s faced regarding security, Zoom has taken a number of steps to beef up security, including the recently announced the acquisition of an end-to-end encryption firm. The improved security is definitely commendable, protecting both their servers and users from unauthorized eavesdropping. End-to-end encryption has been successfully used in the most secure messaging and data sharing systems like Threema and PassHub for years, and there’s no reason why Zoom shouldn’t meet this standard.
But the remote possibility of intercepting Zoom traffic poses much less of a security threat in comparison to unauthorized access through stolen credentials. If the endpoint is compromised, end-to-end encryption would securely deliver content to a hacker.
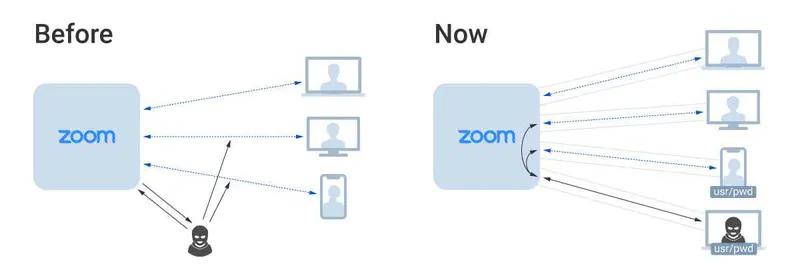
Indeed, Zoom offers the ability to address login insecurity through proper implementation of single sign-on (SSO), transferring the responsibility of secure access management to the companies with business Zoom accounts. Unfortunately, very few companies are taking advantage of that feature.
Without properly implemented SSO with username-less/password-less authentication, Zoom accounts still remain an easy target for phishers. Since the pandemic started, hackers have seized on this vulnerability by creating thousands of fake Zoom domains and stealing more than 500,000 Zoom login credentials (usernames and passwords).
Phishing Zoom accounts is actually fairly simple because:
- All business accounts registered by Zoom have the following typical URL structure: (company URL) corp.zoom.us (where corp is the company name registered with Zoom).
- The registration is for standard non-single sign-on (SSO) logins in the form of email address and password, or using company SSOs in the same username and password format.
That is, they set up fake Zoom login pages and then proceed to capture user credentials when users try to log in.
It’s important to note that hackers’ main target is not accessing Zoom accounts themselves or gaining access to Zoom meetings, but rather to gather user credentials. This type of attack is called credential harvesting. Stolen credentials are re-used later on to compromise other services corporate services. Even companies which integrated their Zoom accounts with their corporate SSO still use usernames and passwords, such as https://citi.zoom.us:
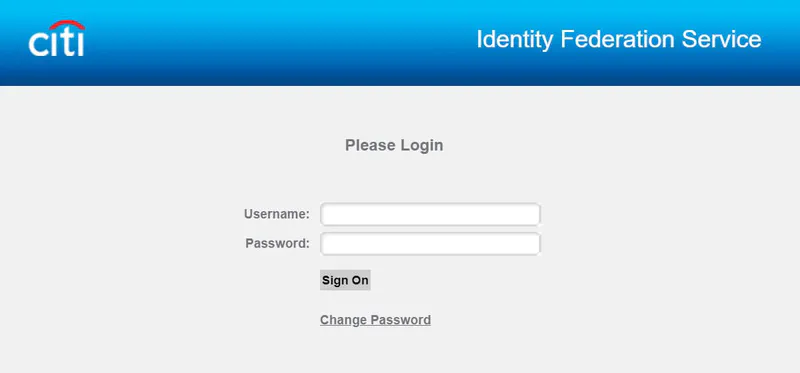
These are still vulnerable to the same phishing attacks.
To avoid this attack vector, companies with business accounts should implement SSO like Gluu with WWPass multifactor authentication, which eliminates the need to authenticate using usernames and passwords and forces all corporate users use passwordless SSO:
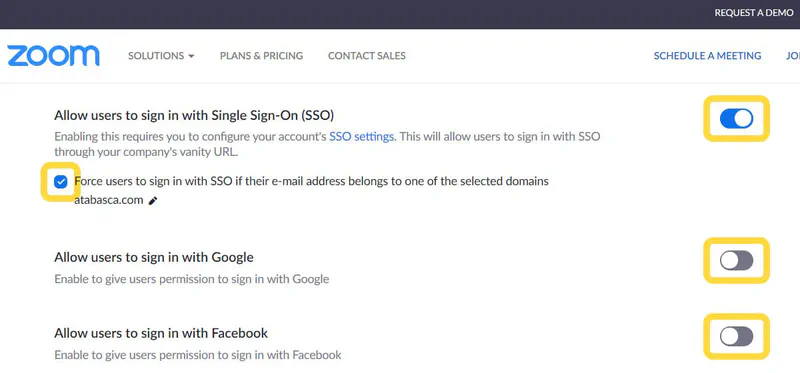
Two questions for Zoom remain: When will free (or at least Professional) accounts get an opportunity to protect their accounts with multi-factor authentication without usernames and passwords to prevent phishing in the same way Business accounts are? And when will Business account holders would get a similar functionality without the need to have SSO?